Machine Type: 7944-AC1, Serial No.:KQ55F8D Product name: IBM System x3550 M3 server
Warranty expires July 8 2014, 1-800-426-7378
UpdateXpress (http://www-933.ibm.com/support/fixcentral/systemx/downloadFixes)
/opt/ibm/uxspi440.rhel6
IMM Management (http://www-933.ibm.com/support/fixcentral/systemx/downloadFixes)
IMM Users Guide (pdf)
MegaRAID Applications -> System Tools -> MegaRAID Storage Manager StartUpGuiUsername: rootPwd:root passwd
/usr/local/MegaRAID Storage Manager/startupui.sh
Local system engineers: Dave Peterson 604-297-2410(o), 604-551-5116(c) or Duncan Furniss
F1 - Setup Alt-F1 - Sysboot
To start IBM Director Server manually, run /opt/ibm/director/bin/twgstart
ServeRAID Adapter Quick Reference
DISKS Info

---------------------------------------------------------------------------------
| 146GB | 146GB | |
-------------------------------- ----------------------- |
| 146GB | empty | DVD | |
--------------------------------------------------------------------------------------
/dev/sdb mounted from XRAID
[root@kratos log]# gdisk -l /dev/sdb
GPT fdisk (gdisk) version 0.8.6
Partition table scan:
MBR: protective
BSD: not present
APM: not present
GPT: present
Found valid GPT with protective MBR; using GPT.
Disk /dev/sdb: 4883808256 sectors, 2.3 TiB
Logical sector size: 512 bytes
Disk identifier (GUID): 9823DDE2-6DFF-4AA6-AF6B-85A8E4F6591A
Partition table holds up to 128 entries
First usable sector is 34, last usable sector is 4883808222
Partitions will be aligned on 8-sector boundaries
Total free space is 0 sectors (0 bytes)
Number Start (sector) End (sector) Size Code Name
1 34 4883808222 2.3 TiB 8E00
/etc/fstab:
[root@kratos log]# cat /etc/fstab
# Accessible filesystems, by reference, are maintained under '/dev/disk'
# See man pages fstab(5), findfs(8), mount(8) and/or blkid(8) for more info
#
/dev/mapper/rhel_kratos-root / xfs defaults 1 1
UUID=8530b48b-5b56-4200-bd6f-b8212e7b2b21 /boot xfs defaults 1 2
UUID=26DA-0C3A /boot/efi vfat umask=0077,shortname=winnt 0 0
#/dev/mapper/rhel_kratos-home /home xfs defaults 1 2
/dev/mapper/rhel_kratos-swap swap swap defaults 0 0
/dev/mapper/VolGroup02-LogVol00 /khome2 ext4 defaults 1 2
/dev/mapper/VolGroup02-LogVol01 /khome ext4 defaults 1 2
#/dev/mapper/VolGroup02-LogVol02 /newton ext4 defaults 1 2
/dev/mapper/VolGroup02-LogVol03 /kahome ext4 defaults 1 2
/libvirt /export/libvirt none bind
192.168.1.29:/home /home nfs4 rw,rsize=32768,wsize=32768,hard,intr,bg,tcp,acl
192.168.1.29:/home2 /home2 nfs4 rw,rsize=32768,wsize=32768,hard,intr,bg,tcp,acl
192.168.1.29:/ahome /ahome nfs4 rw,rsize=32768,wsize=32768,hard,intr,bg,tcp,acl
System Info
empty DIMM slots: 1,4,7,10-18
F1 - Setup F2 - Diagnostics F12 - Select boot device
|
|--> Ctl-H => WebBIOS <--- allows RAID configuration
System x3550 M3
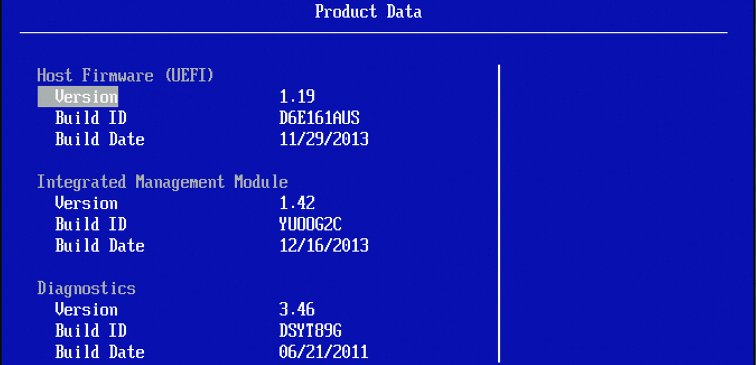
UEFI Build Ver: 1.19 IMM Build Ver: 1.42 Diagnostics Build Ver: 3.46
1 CPU Package Available at 5.86GT/s Link Speed
Machine Type/Model 7944AC1
System Serial Number KQ55F8D
UUID Number F400E69AB0973D108C3C901D4B90B2C9
Processor Summary
Precessor Speed 2.40 GHz
QPI Link Speed 5.86 GT/s
Memory
Operational Mode Independent
Operational Speed 1067 MHz
Total Memory Size 24576 MB
12-03-05 nfs Info
- /var/lib/nfs/rmtab: each line shows the client's name and the file system imported from this server;
- /var/lib/nfs/etab: the /etc/exports file only contains a wish list. etab is created by exportfs. It contains on each line detailed information about the options used when exporting a file system towards a single client. It's the reference file used by rpc.mountd when started
- /proc/fs/nfs/exports contains the clients list as known by the kernel
- /var/lib/nfs/xtab: Use for accuracy when etab holds client names and machines groups with wildcards. This file only contains explicit machine names.
11-12-22 Reboot Problem
- won't shut down properly with reboot command
kratos reboot needs to be done via "
/sbin/reboot.orig --force"
Solution (which did not work for me even though appears to be identical problem):
An option in multipath.conf that instructs it to fail I/O when multipathd isn't running -
# See https://bugzilla.redhat.com/show_bug.cgi?id=662433
# System hang on shutdown when iSCSI devices in use. Comment 32 suggests this.
queue_without_daemon no
It would appear the problem is that just before shutdown the kernel sends a sync to all block devices. Even though file systems (except /) are unmounted , multipathd and the network are down at this point, the iSCSI block devices still exist. So the kernel sends off a sync to the (disconnected) iSCSI devices. The kernel side of the multipath driver then blocks waiting for a path to the iSCSI devices to complete the sync operation. It will wait forever.
'queue_without_daemon no' makes it fail the I/O to the devices instead of blocking for a path.
11-06-29 Currently E5620 @ 2.40 GHz 2x(4 Core), 24GB RAM, mirrored 146GB disks with hot spare.
3 free memory slots. 146 GB, 10K disks are FRU 43W7538.
Sales Order Number: xxx, Date: 2011-06-xx
MAC Address 1: E4:1F:13:B9:DD:C8 eth0
MAC Address 2: E4:1F:13:B9:DD:CA eth1
MAC Address 3: 5C:F3:FC:39:EC:3C eth2
MAC Address 4: 5C:F3:FC:39:EC:3E eth3
eth0 Link encap:Ethernet HWaddr E4:1F:13:B9:DD:C8
inet addr:142.103.236.15 Bcast:142.103.255.255 Mask:255.255.255.0
eth1 Link encap:Ethernet HWaddr E4:1F:13:B9:DD:CA
inet addr:10.20.14.15 Bcast:10.255.255.255 Mask:255.255.255.0
eth2 Link encap:Ethernet HWaddr 5C:F3:FC:39:EC:3C
eth3 Link encap:Ethernet HWaddr 5C:F3:FC:39:EC:3E
PartNo/
Feature Qty Description
------- --- ---------------------------------------------------------------
7944D4U 1 x3550 M3, Xeon 6C X5650 95W 2.4GHz/1333MHz/4MB, 1x4GB,
O/Bay 2.5in HS SAS/SATA, 675W p/s, Rack
59Y3952 1 x3550 M3 R2 ODD Kit
49Y1406 5 4GB (1x4GB PC3L-10600 CL9 ECC DDR3-1333MHz LP RDIMM
46M1076 1 Dual Port 1GB Eth Daughter Card
42D0677 3 IBM 146GB 15K 6Gbps SAS 2.5" SSF Slim-HS HDD
46M0902 1 IBM UltraSlim Enhanced SATA Multiburner
81Y6558 1 IBM 465W Redundant AC Power Supply
1 3 year Onsite Repair next day
12-01-10 kerberos/NFSv4 setup
Basically followed method at
Kerberos/LDAP/NFSv4 HOWTO)
with further info at
How to configure nfsv4 with kerberos in RHEL and
Part II)
/usr/bin/system-config-date
yum install krb5-server
cd /etc
cp krb5.conf krb5.conf.orig
vim krb5.conf
cd /var/kerberos/krb5kdc/
cp kdc.conf kdc.conf.orig
vim kdc.conf
cp kadm5.acl kadm5.acl.orig
vim kadm5.acl
vim /etc/gssapi_mech.conf
yum install krb5-libs.x86_64 krb5-workstation.x86_64 pam_krb5.x86_64 cyrus-sasl-gssapi.x86_64 openldap-clients.x86_64
vim kadm5.acl
vim /etc/gssapi_mech.conf
kdb5_util create -s
vim /etc/krb5.conf
vim /var/kerberos/krb5kdc/kdc.conf
vim /var/kerberos/krb5kdc/kadm5.acl
/usr/bin/authconfig-tui
kadmin.local -q "addprinc root/admin"
chkconfig kadmin on
service kadmin start
chkconfig krb5kdc on
service krb5kdc start
[root@kratos krb5kdc]# kinit
kinit: Client not found in Kerberos database while getting initial credentials
[root@kratos krb5kdc]# kinit root/admin
Password for root/admin@PHAS.UBC.CA:
[root@kratos krb5kdc]# klist
Ticket cache: FILE:/tmp/krb5cc_0
Default principal: root/admin@PHAS.UBC.CA
Valid starting Expires Service principal
01/12/12 09:55:48 01/13/12 09:55:48 krbtgt/PHAS.UBC.CA@PHAS.UBC.CA
renew until 01/12/12 09:55:52
[root@kratos krb5kdc]# kadmin.local
Authenticating as principal root/admin@PHAS.UBC.CA with password.
kadmin.local: addprinc -randkey nfs/kratos.phas.ubc.ca
WARNING: no policy specified for nfs/kratos.phas.ubc.ca@PHAS.UBC.CA; defaulting to no policy
Principal "nfs/kratos.phas.ubc.ca@PHAS.UBC.CA" created.
kadmin.local: ktadd nfs/kratos.phas.ubc.ca
Entry for principal nfs/kratos.phas.ubc.ca with kvno 2, encryption type aes256-cts-hmac-sha1-96 added to keytab WRFILE:/etc/krb5.keytab.
Entry for principal nfs/kratos.phas.ubc.ca with kvno 2, encryption type aes128-cts-hmac-sha1-96 added to keytab WRFILE:/etc/krb5.keytab.
Entry for principal nfs/kratos.phas.ubc.ca with kvno 2, encryption type des3-cbc-sha1 added to keytab WRFILE:/etc/krb5.keytab.
Entry for principal nfs/kratos.phas.ubc.ca with kvno 2, encryption type arcfour-hmac added to keytab WRFILE:/etc/krb5.keytab.
Entry for principal nfs/kratos.phas.ubc.ca with kvno 2, encryption type des-hmac-sha1 added to keytab WRFILE:/etc/krb5.keytab.
Entry for principal nfs/kratos.phas.ubc.ca with kvno 2, encryption type des-cbc-md5 added to keytab WRFILE:/etc/krb5.keytab.
kadmin.local: q
Check principal exists:
[root@kratos etc]# klist -k
Keytab name: WRFILE:/etc/krb5.keytab
KVNO Principal
---- --------------------------------------------------------------------------
2 nfs/kratos.phas.ubc.ca@PHAS.UBC.CA
2 nfs/kratos.phas.ubc.ca@PHAS.UBC.CA
2 nfs/kratos.phas.ubc.ca@PHAS.UBC.CA
2 nfs/kratos.phas.ubc.ca@PHAS.UBC.CA
2 nfs/kratos.phas.ubc.ca@PHAS.UBC.CA
2 nfs/kratos.phas.ubc.ca@PHAS.UBC.CA
Create service keys for kadmin/admin and kadmin/changepw. Not sure if this step was really needed.
[root@kratos]# kadmin.local -q "ktadd -k /var/kerberos/krb5kdc/kadm5.keytab kadmin/admin kadmin/changepw"
Authenticating as principal root/admin@PHAS.UBC.CA with password.
Entry for principal kadmin/admin with kvno 3, encryption type aes256-cts-hmac-sha1-96 added to keytab WRFILE:/var/kerberos/krb5kdc/kadm5.keytab.
Entry for principal kadmin/admin with kvno 3, encryption type aes128-cts-hmac-sha1-96 added to keytab WRFILE:/var/kerberos/krb5kdc/kadm5.keytab.
Entry for principal kadmin/admin with kvno 3, encryption type des3-cbc-sha1 added to keytab WRFILE:/var/kerberos/krb5kdc/kadm5.keytab.
Entry for principal kadmin/admin with kvno 3, encryption type arcfour-hmac added to keytab WRFILE:/var/kerberos/krb5kdc/kadm5.keytab.
Entry for principal kadmin/admin with kvno 3, encryption type des-hmac-sha1 added to keytab WRFILE:/var/kerberos/krb5kdc/kadm5.keytab.
Entry for principal kadmin/admin with kvno 3, encryption type des-cbc-md5 added to keytab WRFILE:/var/kerberos/krb5kdc/kadm5.keytab.
Entry for principal kadmin/changepw with kvno 3, encryption type aes256-cts-hmac-sha1-96 added to keytab WRFILE:/var/kerberos/krb5kdc/kadm5.keytab.
Entry for principal kadmin/changepw with kvno 3, encryption type aes128-cts-hmac-sha1-96 added to keytab WRFILE:/var/kerberos/krb5kdc/kadm5.keytab.
Entry for principal kadmin/changepw with kvno 3, encryption type des3-cbc-sha1 added to keytab WRFILE:/var/kerberos/krb5kdc/kadm5.keytab.
Entry for principal kadmin/changepw with kvno 3, encryption type arcfour-hmac added to keytab WRFILE:/var/kerberos/krb5kdc/kadm5.keytab.
Entry for principal kadmin/changepw with kvno 3, encryption type des-hmac-sha1 added to keytab WRFILE:/var/kerberos/krb5kdc/kadm5.keytab.
Entry for principal kadmin/changepw with kvno 3, encryption type des-cbc-md5 added to keytab WRFILE:/var/kerberos/krb5kdc/kadm5.keytab.
Make sure rpcgssd and rpcsvcgssd are configured to start on reboot and then start them.
[root@kratos init.d]# chkconfig --list | grep gss
rpcgssd 0:off 1:off 2:off 3:on 4:on 5:on 6:off
rpcsvcgssd 0:off 1:off 2:on 3:on 4:on 5:on 6:off
[root@kratos init.d]# service rpcgssd start
Starting RPC gssd: [ OK ]
[root@kratos init.d]# service rpcsvcgssd start
Starting RPC svcgssd: [ OK ]
kerberos/NFSv4 setup - Client Configuration
phasadmin@javelin:~$ sudo apt-get install krb5-user
phasadmin@javelin:~$ sudo vim /etc/krb5.conf
[libdefaults]
default_realm = PHAS.UBC.CA
# The following krb5.conf variables are only for MIT Kerberos.
krb4_config = /etc/krb.conf
krb4_realms = /etc/krb.realms
kdc_timesync = 1
ccache_type = 4
forwardable = true
proxiable = true
[realms]
PHAS.UBC.CA = {
kdc = kratos.phas.ubc.ca
kdc = ldap.phas.ubc.ca
admin_server = kratos.phas.ubc.ca
default_domain = phas.ubc.ca
}
[domain_realm]
.phas.ubc.ca = PHAS.UBC.CA
phas.ubc.ca = PHAS.UBC.CA
.physics.ubc.ca = PHAS.UBC.CA
physics.ubc.ca = PHAS.UBC.CA
.astro.ubc.ca = PHAS.UBC.CA
astro.ubc.ca = PHAS.UBC.CA
Encountered and error when doing client config on ubuntu:
root@javelin:/etc# kadmin
Authenticating as principal root/admin@PHAS.UBC.CA with password.
Password for root/admin@PHAS.UBC.CA:
kadmin: GSS-API (or Kerberos) error while initializing kadmin interface
Solved this by getting clocks in sync.
Run kadmin on client:
khroot@javelin:/etc# kadmin
Authenticating as principal root/admin@PHAS.UBC.CA with password.
Password for root/admin@PHAS.UBC.CA:
kadmin: addprinc -randkey nfs/javelin.phas.ubc.ca
WARNING: no policy specified for nfs/javelin.phas.ubc.ca@PHAS.UBC.CA; defaulting to no policy
add_principal: Principal or policy already exists while creating "nfs/javelin.phas.ubc.ca@PHAS.UBC.CA".
kadmin: ktadd -k /etc/krb5.keytab nfs/javelin.phas.ubc.ca
Entry for principal nfs/javelin.phas.ubc.ca with kvno 2, encryption type AES-256 CTS mode with 96-bit SHA-1 HMAC added to keytab WRFILE:/etc/krb5.keytab.
Entry for principal nfs/javelin.phas.ubc.ca with kvno 2, encryption type AES-128 CTS mode with 96-bit SHA-1 HMAC added to keytab WRFILE:/etc/krb5.keytab.
Entry for principal nfs/javelin.phas.ubc.ca with kvno 2, encryption type Triple DES cbc mode with HMAC/sha1 added to keytab WRFILE:/etc/krb5.keytab.
Entry for principal nfs/javelin.phas.ubc.ca with kvno 2, encryption type ArcFour with HMAC/md5 added to keytab WRFILE:/etc/krb5.keytab.
Entry for principal nfs/javelin.phas.ubc.ca with kvno 2, encryption type DES with HMAC/sha1 added to keytab WRFILE:/etc/krb5.keytab.
Entry for principal nfs/javelin.phas.ubc.ca with kvno 2, encryption type DES cbc mode with RSA-MD5 added to keytab WRFILE:/etc/krb5.keytab.
kadmin: q
root@javelin:/etc# klist -k
Keytab name: WRFILE:/etc/krb5.keytab
KVNO Principal
---- --------------------------------------------------------------------------
2 nfs/javelin.phas.ubc.ca@PHAS.UBC.CA
2 nfs/javelin.phas.ubc.ca@PHAS.UBC.CA
2 nfs/javelin.phas.ubc.ca@PHAS.UBC.CA
2 nfs/javelin.phas.ubc.ca@PHAS.UBC.CA
2 nfs/javelin.phas.ubc.ca@PHAS.UBC.CA
2 nfs/javelin.phas.ubc.ca@PHAS.UBC.CA
Edit /etc/default/nfs-common and make sure IDMAPD and GSSD lines are as follows:
NEED_IDMAPD=yes
NEED_GSSD=yes
Added this on KDC (kratos):
[root@kratos init.d]# kadmin
Authenticating as principal root/admin@PHAS.UBC.CA with password.
Password for root/admin@PHAS.UBC.CA:
kadmin: addprinc -randkey nfs/javelin.phas.ubc.ca
WARNING: no policy specified for nfs/javelin.phas.ubc.ca@PHAS.UBC.CA; defaulting to no policy
add_principal: Principal or policy already exists while creating "nfs/javelin.phas.ubc.ca@PHAS.UBC.CA".
root@javelin:~# apt-get install libpam-krb5
11-09-22 Will not shutdown
Contacted IBM re shutdown problem. When I do a reboot or a shutdown, it never shuts down. I need to toggle the power swtch. Assigned ref# 41JK4PS.
11-09-22 Disk Failure
Contacted IBM re disk problem. They had me run DSA
(/opt/ibm/dsa/ibm_utl_dsa_dsyt85t-3.40_portable_rhel6_x86-64.bin)
https://www-947.ibm.com/support/entry/myportal/docdisplay?lndocid=SERV-DSA
He (ptherrie@ca.ibm.com, Phillipe Therrien)emailed back that a disk had failed (I knew this from the noise and yellow light on the drive). They will courier out a new drive today.
New drive is S/N
System Info
Please note that portmap service is not required for NFSv4.
NFS Server Configuration GUI Tool
# system-config-nfs
Open TCP port # 2049 which is used by NFSv4. Add the following lines,
ensuring that they appear before the final LOG and DROP lines for the
RH-Firewall-1-INPUT chain:
-A RH-Firewall-1-INPUT -s 192.168.1.0/24 -m state --state NEW -p tcp --dport 2049 -j ACCEPT
A Note About User Management
Use OpenLDAP for user management for large number of users. If you have a
small number of NFS clients add them to your systems using the useradd command.
Make sure UID and GID matches correctly. For example, if user vivek (UID=500)
is part of group vivek (gid=500) and sales group (Gid=502) on the NFSv4 server,
then use the following command to add user to NFSv4 client:
# grep -q '^sales' /etc/group || /usr/sbin/groupadd -g 502 sales
# /usr/sbin/useradd -s /bin/bash -d /sales -M -u 500 -g 500 -G 502 sales
# su - sales
$ pwd
$ ls && cd mumbai && >testfile && ls -l testfile && rm testfile
The above command matches client and server UIDs and GIDs.
Otherwise you will get permission denied message on NFSv4 clients.
11-09-02
Installing : nscd-2.12-1.25.el6_1.3.x86_64
Installing : pam_ldap-185-8.el6.x86_64
Installing : nss-pam-ldapd-0.7.5-7.el6.x86_64
check //usr/share/netcf/iptables-forward-bridged
11-06-28
Run IBM UpdateXpress.
[root@kratos]# /opt/IBM/UpdateXpress/uxspi440.rhel6
Hard Disk Drive ibm_fw_hdd_sas-1.08.01_linux_32-64 32,927
IMM ibm_fw_imm_yuoo91k-1.25_linux_32-64 36,050
Converged Netwk Adapter qlgc_fw_nic_qle8142-1.01.94_linux_32-64 4,323
UXSP ibm_utl_uxsp_d6sp07a-1.60_rhel6_32-64 1,328
SAS ibm_fw_mpt2sas_1.07_linux_32-64 1,466
SAS ibm_fw_sraidbr_10i-2.72_linux_32-64 1,264
SAS ibm_fw_mptsas_3g-sashba-2.72_linux_32-64 1,109
SAS ibm_fw_sraidbr_10il-v2-2.72_linux_32-64 1,058
SATA ibm_fw_pmcraid_1.03_linux_32-64 2,002
ServeRAID ibm_fw_sraidmr_10i-10is-11.0.1-0033a_linux_32-64 4,643
SAS ibm_fw_sraidmr_10m-11.0.1-0033a_linux_32-64 4,636
SAS ibm_fw_sraidmr_m5000-12.12.0-0039_linux_32-64 3,208
Diagnostics ibm_fw_dsa_dsyt83d-3.33_linux_32-64 96,853
UEFI ibm_fw_uefi_d6e150c-1.11_linux_32-64 3,653
SAS ibm_fw_sraidmr_1015-20.10.1-0022_linux_32-64 2,951
Network brcm_fw_nic_2.1.6a_linux_32-64 8,821
IMM ibm_fw_imm_yuoo57h_linux_32-64 29,997
11-06-28
useradd rap
vim /etc/inittab (change initial runlevel to 5)
cd /usr/local/src
wget --no-check-certificate --user=rap --ask-password https://www.phas.ubc.ca/sysadmin/Computers/00_Servers/rhel/satellite_setup.pl
chmod +x satellite_setup.pl
./satellite_setup.pl
yum groupinstall "General Purpose Desktop"
yum groupinstall Desktop
cd /opt/IBM/UpdateXpress
./uxspi440.rhel6
FIX THIS !!!
Installed RAID monitoring Software (
ServeRAID MR Support CD)
cd /usr/local/src
mount -o loop ibm_sw_sraidmr_10.35_anyos_32-64.iso /mnt/iso
yum install libXp
yum install net-snmp
cd /mnt/iso/MSM/Linux/
./install.sh
[root@omega Linux]# rpm -qa | grep -i mega
MegaRAID_Storage_Manager-2.91-03
|
NOTES:
UPDATE NEEDED DISASTER RECOVERY
- Install a new server.
- Load RHEL V6.
Additional, non-critical items to take care of:
- Install APCUPSD
|
UPDATE NEEDED DISASTER RECOVERY
- Install a new server.
- Load RHEL V5 (or newer).
- Make sure you select to install the web server and associated modules.
- Make sure you select to install the mysql server and associated modules.
- Copy over backup files from alpha:/home/backups/www (these files are rsync'd daily).
- Make sure mysqld and httpd are started.
- Make sure to set a root password for mysqld (admin -u root password newpassword).
- Install phpMyAdmin. Create phpMyAdmin dbases: mysql -u root -p < create_tables_mysql_4_1_2+.sql
- Install php-mbstring package from redhat network package archive so phpMyAdmin doesn't complain.
- Get include files installed into /php/includes.
- Check /etc/php.ini configuration file.
- Check /etc/http/conf configuration files including certificate files.
/etc/http/conf/ssl.crt/www.phas.ubc.ca.crt
/etc/http/conf/ssl.crt/gd_bundle.crt
/etc/http/conf/ssl.key/www.phas.ubc.ca.key
- Install MySQL-zrm.
Additional, non-critical items to take care of:
- Install APCUPSD
- Check webalizer installation (web stats).
|
BIOS Settings - 14-07-11